Threat actors have found continuous success using package delivery services as SMS phishing lures since the start of the COVID-19 pandemic and package delivery phishing attacks are the number one harvester of credit cards that WMC Global is currently seeing. Scammers now gravitate towards any new courier as a lure because of the sheer effectiveness of the campaigns. These lures are often used to perform call back scams but consumers get wise to the same attack content, resulting in threat actors needing to diversify and increase their portfolio of campaigns. Introducing Evri, the latest UK courier company to be heavily targeted and brand abused for credential phishing attacks.
Evri is the new name of rebranded courier service Hermes. It can temporarily be confusing for consumers when a company rebrands, which is why threat actors have chosen to act during this time period. WMC Global continues to see Hermes SMS phishing campaigns but, large-scale Evri SMS phishing campaigns are becoming more prevalent.
The Attack
We have captured an end-to-end campaign user experience below, which allows us to fully understand and investigate the attack chain.
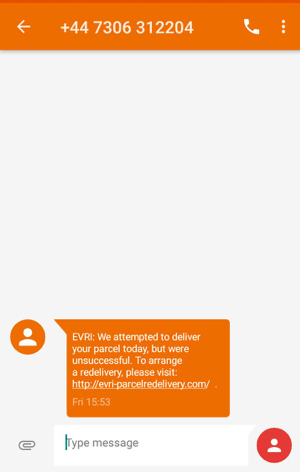 Figure 1: Evri SMS phishing text message
Figure 1: Evri SMS phishing text message
All SMS phishing campaigns start with a text message sent to a victim's phone number (example: Figure 1). This scam uses a generic message that has already been employed in several other courier scams. This overlap in messaging text gives a strong indication of a common threat actor group running the Evri campaigns as well as other UK phishing campaigns.
Once a victim clicks on the link, they are sent to a website which is a pixel-perfect copy of the legitimate Evri website.
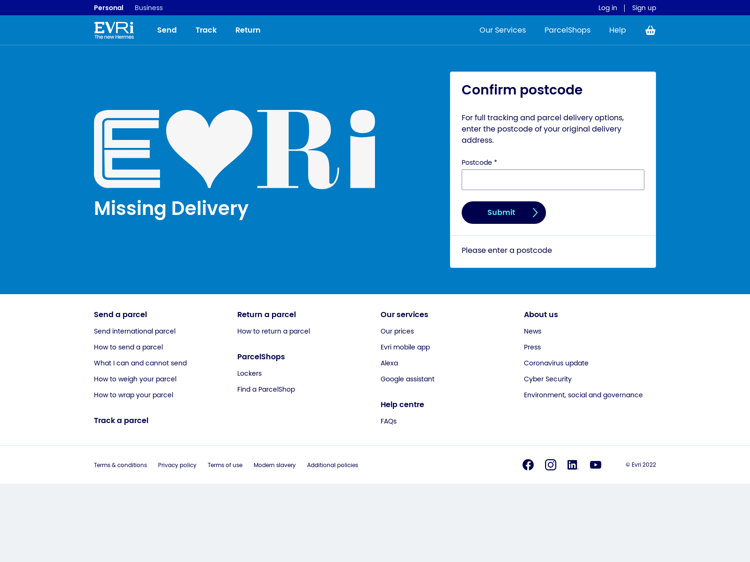 Figure 2: Evri phishing website homepage
Figure 2: Evri phishing website homepage
There are several ways in which the threat actor can proceed after they successfully steal a user’s credentials. Some will sell these credentials to other scammers on the dark web for future monetization. The most common path, however, is to perform a call-back scam, where the threat actor calls the victim directly. These scams use a few lures, but often rely on the “safe account” ruse, whereby the threat actor pretends to be from the victim’s bank and states that their money is at risk, and it needs to be transferred into a safe account. This “safe account” is owned by the threat actor and once the victim sends the payment, the scammer will send the money into their mule network to hide the funds in a web of complex money mixers, offshore accounts, and front companies (plus many other techniques) to avoid banks and law enforcement from tracking the money in the future.
THE PHISHING KITS
WMC Global detects, analyzes, and indexes phishing kits, enabling us to understand the threat actors’ attack source code, which can give powerful insight into threat actor behavior. We have detected multiple unique Evri kits which are currently deployed, which all follow the basic principles of tricking a user into disclosing personally identifiable information (PII). The details frequently include name, address, bank details, and mobile number. Investigating these kits allows us to understand how the sites operate, how well they are built, and we can extract vital clues to attribute these kits back to developers or individuals involved in their production.
Investigating one particular Evri kit, we can see that a number of anti-bot checks take place initially. These checks are to prevent automated scanners from detecting the website as malicious and can work in a variety of ways. This kit specifically has several features including an IP block list, user agent block list, anti- scanning functionality, and a http header checker. The number and variety of these anti-bot features give a strong indication that the developing threat actor is attempting to evade detection for as long as possible as ensuring the longevity of their website allows more victims to fall for the scam. Increasing rh yield of each campaign is vital for threat actors because setting up new domains and infrastructure is an investment of both time and money.
The kit also contains a configuration file which allows the controlling threat actor to adapt how the phishing website works without requiring coding skills. The configuration file options for this Evri kit allow different types of victim log storage, enabling exfiltration to Telegram and adjustments to the fake tracking code or monetary demand cost.
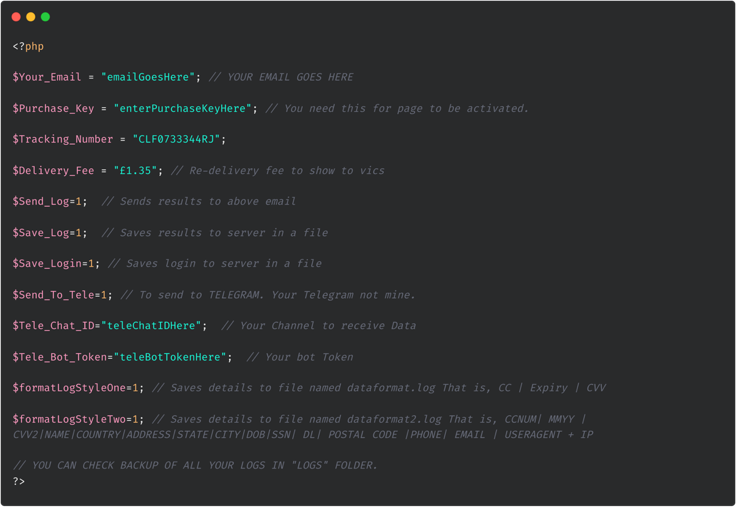 Figure 3: Configuration file code preview
Figure 3: Configuration file code preview
WMC Global has visibility of a huge number of phishing kits using our KITIntel product which allows us to observe consistently overlapping features between them. We detected a string in one of the Evri phishing kits which was the threat actors' signature. The threat actor is known under the alias ‘Dwi P.D’ which can be seen in the newly released Evri kit below (Figure 4). This actor's signature can also be found in phishing kits which target Australia Post, Canada Post, Santander Bank, Monzo Bank, Allied Irish Banks (AIB), SunCorp, the NHS, USPS, and Wells Fargo.
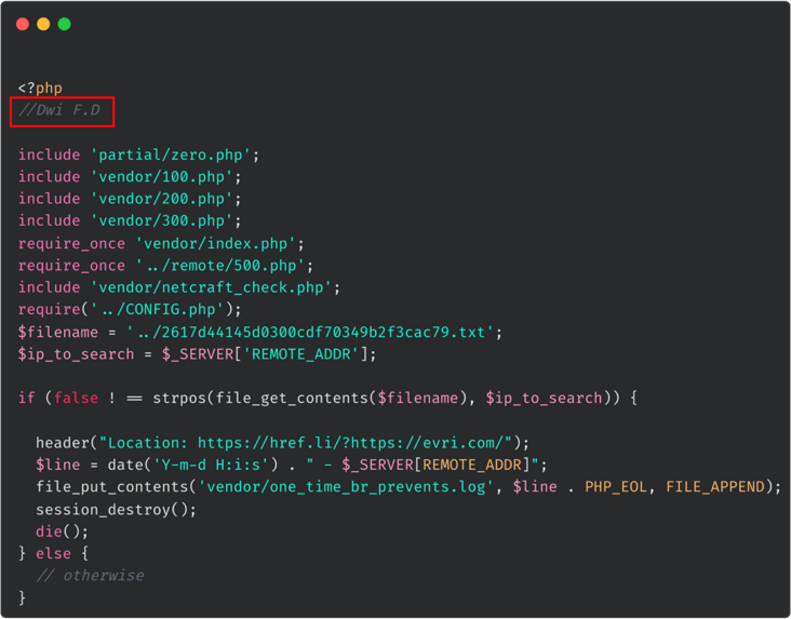 Figure 4: Threat actor "Dwi F.D" signature in the latest Evri kit
Figure 4: Threat actor "Dwi F.D" signature in the latest Evri kit
We have also discovered another alias related to the same actor which is ‘zeroc0d3r’. This alias has been seen in multiple kits and we have recorded several occasions where there is overlap between the ‘Dwi P.D’ and ‘zeroc0d3r’ aliases. Tracking overlaps like this allows us to link multiple kits back to one developing threat actor. Altogether, WMC Global has seen 22 unique kits related to this actor showing the breadth of their reach and the reality of the number of victims they have targeted from their scam pages.
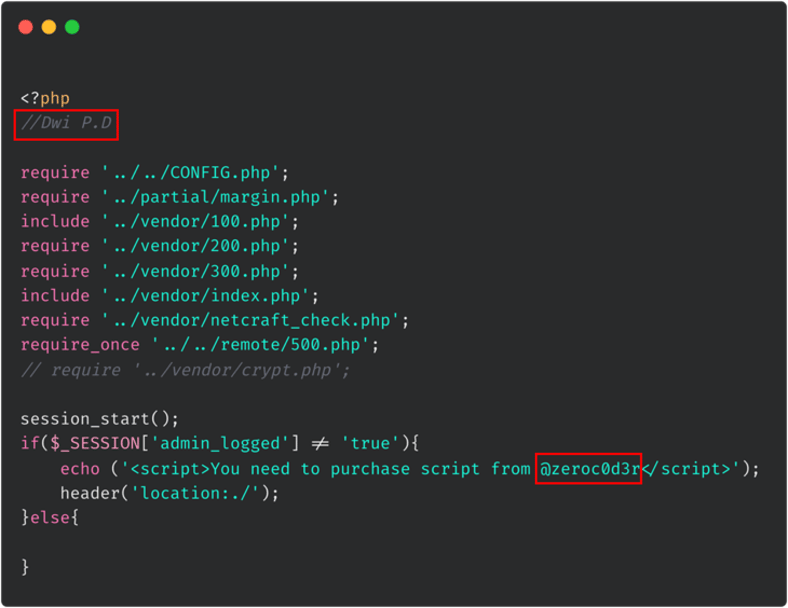 Figure 5: Phishing kit showing both threat actor aliases
Figure 5: Phishing kit showing both threat actor aliases
It is important for consumers to understand the risks of SMS phishing and even more crucial for them to recognize it when they are experiencing an SMS phishing attack.
How to spot a malicious SMS and keep yourself safe:
- If a message feels suspicious or too good to be true, it probably is. Users should familiarize themselves with common signs of a text message scam or smishing attack, including:
- Incorrect spelling or grammar usage, within the message itself or misspelled links or brand names
- Unexpected free offerings - prizes, gift cards, or small business loans
- Contact from government agencies or financial institutions looking to confirm sensitive information through a call or link sent by text -- Government Unemployment Fraud
- Are there are personal details in the SMS? Your name, tracking number, or an order reference number? If not, this is most likely a sign of a scam. Legitimate messages often contain personal details related to the customer or the order. If you are also not expecting a delivery, then it is likely that messages from any courier will be a scam. Go directly to the company's website, never click links within SMS.





